What is layered security and how is it structured?

Would you feel safe if, upon arriving at the airport, only your carry-on luggage is checked, and without any other security screening, you board the plane? Probably not, because you’re aware of the risks and incidents that have occurred at airports. Now think about your business—why settle for basic security solutions when cyber threats are constantly emerging? Just like at the airport, it’s essential to invest in layered security. In this article, we’ll explain what layered security is and how it is structured.
What is layered security?
The layered security strategy originates from a military concept known as Defense in Depth, which argues that it is more effective to have several consecutive defensive lines rather than a single, highly fortified line. In cybersecurity, this concept is applied by implementing multiple layers of security, allowing for defined controls at each layer. This approach ensures that if one layer is compromised, others remain in place to protect critical systems and data, much like how multiple defensive lines would slow down or stop an advancing enemy in a military context.
It focuses on each level of potential threats, providing the security and peace of mind needed to carry out our daily work. The days when a good antivirus was sufficient to combat most threats are long gone.
In addition to supporting the development of telecommunications protocols, this suite serves as a foundation for understanding how to apply security strategies across the entire structure of a network. Just as the failure of one of these layers to provide its respective services means that the higher layers cannot successfully achieve their objectives, a vulnerability that compromises one layer renders any other protective measures taken at higher levels of abstraction ineffective.
We can compare layered security to the layers of an onion: it’s about implementing measures that address vulnerabilities across all layers, ensuring that protocols are properly configured throughout the entire stack, and across all devices involved in the network. Just like peeling back each layer of an onion reveals another layer beneath, layered security ensures that even if one layer is compromised, others remain intact to protect the system.
How is layered security structured?
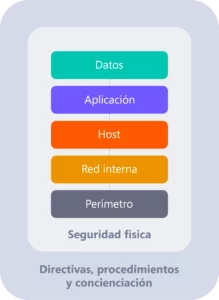
Here are the multiple layers that make up security and enable the implementation of a comprehensive information security strategy, providing you with a complete view of your company’s logical security:
1. Policies, Procedures, and Awareness
- Policies
- Procedures
- Awareness Campaigns
- Cybersecurity Culture
2. Perimeter
Perimeter security is designed to protect the internal network from potential external threats. It focuses on maintaining integrity and security from the outside. The term “perimeter” refers to the boundary between the local intranet and the external world, known as the “Internet.” This boundary is crucial for keeping confidential information and resources out of the reach of the general public and, of course, malicious individuals.
It is aimed at protecting the internal network from external attacks. It encompasses various tools and techniques designed to safeguard an organization’s information technology, closely relating to the internal network and its extended environment. Here are some examples:
- Firewall
- Data Loss Prevention (DLP)
- Intrusion Prevention System (IPS)
- Distributed Denial of Service (DDoS)
- Wireless Security
- Virtual Private Network (VPN)
3. Internal Network
The internal network layer focuses on protecting a local area network (LAN), where devices are interconnected within a confined space. The risks associated with these internal networks are related to the transmission of confidential data. To counteract these risks, the growing practice of segmenting the internal network into security zones through subnetting has been adopted. This strategy helps establish a perimeter in each zone, reducing exposure to potential malicious attacks aiming to access the internal network. Aimed at protecting the internal network from internal attacks, here are some tools:
- Virtual LAN (VLAN)
- Network Access Control (NAC)
- Access Control List (ACL)
- Secure Socket Layer (SSL)
- Network Intrusion Detection System (NIDS)
4. Host
The term “host” refers to computers and servers. In this context, the protection layer focuses on securing the operating system of each computer or server, as well as their specific functions within the network. This layer is responsible for establishing and terminating the various connections between hosts.
In addition to establishing sessions, this layer also provides support such as log management and security tasks. It enables users on different machines to establish sessions with each other. This layer is primarily focused on protecting the devices within the internal network, and the most common solutions include:
- Desktop Management
- Patch Management
5. Application
Application security encompasses the development, integration, and testing of security features within applications to prevent vulnerabilities against threats such as unauthorized access and modification. Some solutions and tools that can help protect applications include:
- Secure Application Development
- Web Application Firewall
- Identity and Access Management (IAM)
- Demilitarized Zone (DMZ)
- Virtual LAN (VLAN)
- Patch Management
6. Data
Data security involves implementing protective measures to safeguard data from unauthorized access, ensuring the confidentiality, integrity, and availability of the database. Best practices for data protection include data encryption, key management, data obfuscation, data segmentation, data masking, as well as establishing access controls for privileged users, conducting audits, and monitoring. Here are some tools that can help safeguard data security:
- Data Loss Prevention (DLP)
- Information Encryption
- Respaldo / Réplica de Información
- Disaster Recovery Plan (DRP)
- Data Access Audit
In summary, each layer encapsulates a set of protocols, equipment, and security techniques that can be deployed to make it more challenging for attackers. Understanding these concepts will enable you to better analyze the level of protection in your company’s network, as well as identify potential vulnerabilities and gaps.
If you want to learn more about how to implement a comprehensive security strategy to prevent issues and detect vulnerabilities in a timely manner, icorp can help you. Contact Us.
This article has been translated using AI and may include errors.






